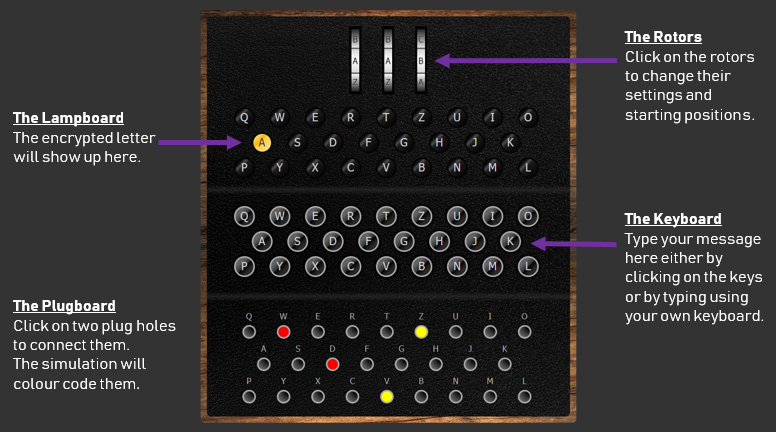
Enigma Cipher Machines This page is about the famous Enigma cipher machine, well known for the vital role it played during WWII Below are descriptions of the various models, their manufacturers, some accessories, patents, computer simulations and codebreaking There is no such thing as the Enigma In fact, Enigma is the brand name of a series of cipher machines, I'm trying to improve my C Enigma Machine, either by shortening the code or finding more efficient ways to complete certain things Be aware I have very basic C vocabulary Are there any major flaws in my code? EnigmaUhr ("SteckerUhr") For starters you may even ignore settings at all, as the Enigma will code anyway as soon as there is valid text input Just start a new session or reload the page, enter your message on the lefthand side and observe the output to the right You can also see the rotors step at every (codeable) keystroke To decipher the output, copy it and feed it to

Enigma Machine Wikipedia
The enigma code cipher
The enigma code cipher- I suspect that the word "Enigma" here doesn't refer to an enigma machine Most likely the cipher is encrypted using some more basic cipher But the ciphertext is very short, and the number of unknowns is too great, so without more information, finding a credible solution is unlikely Running the ciphertext through quipqiup gives a number ofMiscellaneous Enigma Simulator Information This software is an exact simulation of the 3rotor Wehrmacht (Army and Air Force) Enigma, the 3rotor Kriegsmarine (Navy) M3, also called Funkschlussel M, and the famous 4rotor Kriegmarine M4 Enigma cipher machine, used during World War II from 1939 until 1945 The sim has a very authentic feeling




Enigma Machine Emulator 101 Computing
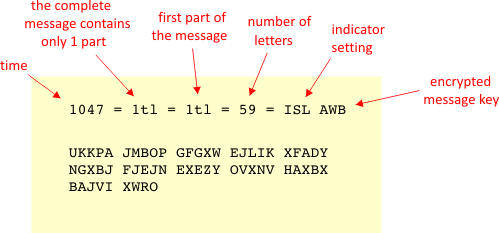
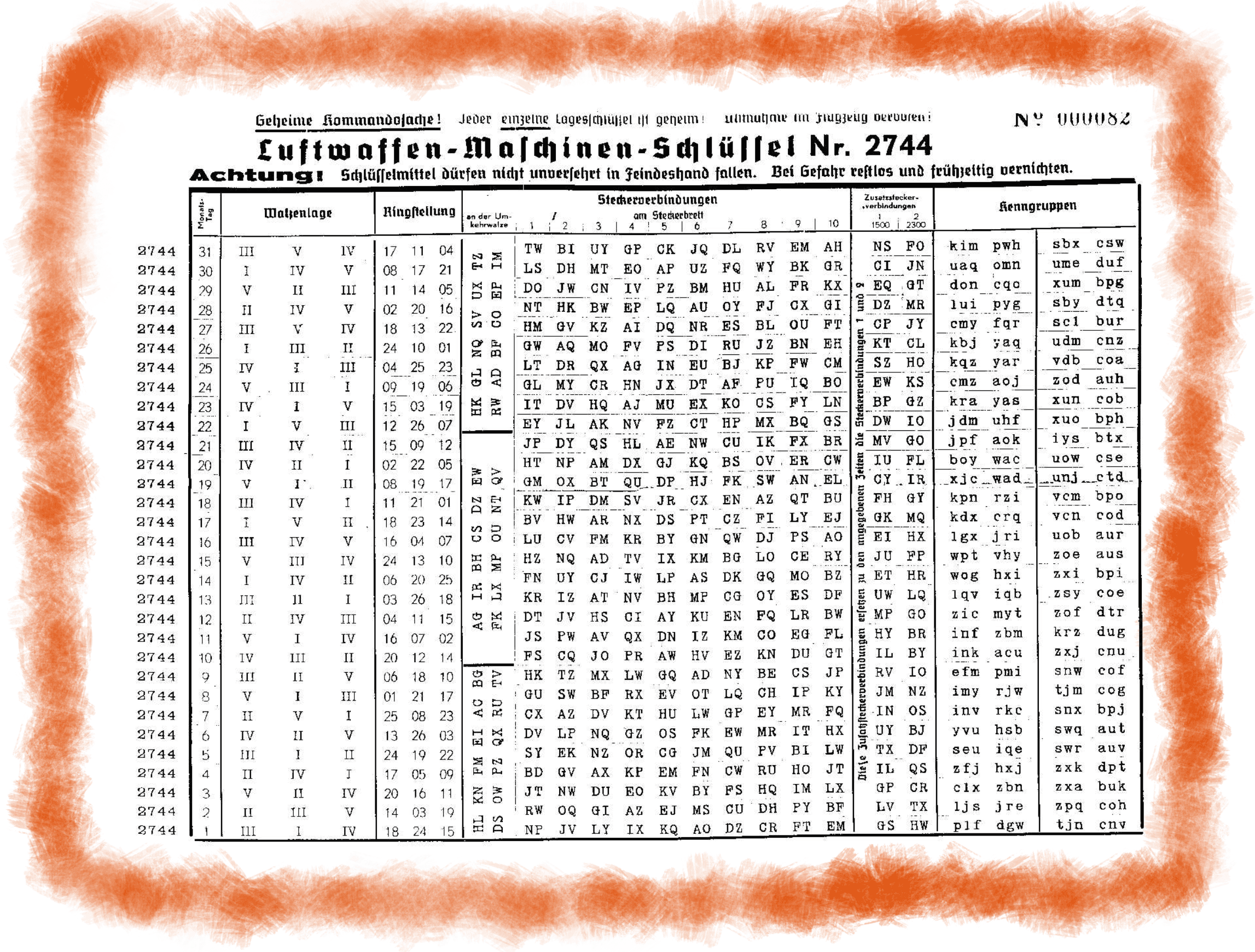
Enigma decoder Decrypt and translate enigma online The Enigma cipher machine is well known for the vital role it played during WWII Alan Turing and his attempts to crack the Enigma machine code changed history Nevertheless, many messages could not be decrypted until today Alphabetical substitution Hex to Base64 Unicode lookup Crockford's Base32 URL encode CryptiiDigicaSolutions / EnigmaCode Star 26 Code Issues Pull requests Cracking the Enigma Code cryptanalysis enigma enigmasimulator enigmamachine enigmacipher enigmaintelligence Updated ;When using mechanical cipher machines, such as the German Enigma, it was common practice to supply the daily settings of the machine, such as the order of the wheels and the initial position, on a socalled key sheet or key listIn most cases, a key sheet contained the settings for several days — sometimes even a full month — in advance Please note that a key sheet is not the same as a
The Enigma Code was invented by Arthur Scherbius in 1918, and took the world by storm due to its use in World War 2 The Germans used a very complicated machine called an Engima Machine in order to encrypt their messages The Polish managed to find out how to decrypt the messages, but the Germans then stepped up their security by changing the cipher every day This meant thatCodes and Ciphers The Enigma cipher machine These pages give an introduction to substitution ciphers and then go on to explain exactly how the Enigma machine worked and how it was used At present the pages are as follows 1 Substitution ciphers and the principle of the Enigma with a detailed example illustrating how the Enigma enciphers letters 2 The components of the Enigma*/ /* The Enigma machines were a family of portable cipher machines with rotor scramblers Good operating procedures, properly enforced, would have made the cipher unbreakable However, most of the German armed and secret services and civilian agencies that used Enigma employed poor procedures and it was these that allowed the cipher to be broken The German plugboardequipped Enigma
Caesar cipher is in fact a Vigenere cipher with a 1letter long key Vigenere code uses longer keys that allows the letters to be crypted in multiple ways The frequency analysis is no more enough to break a codeThe Principle of the Enigma Tony Sale's Codes and Ciphers This is Page 1 of Tony Sale's sequence of pages explaining the Enigma machine This page gives an introduction to substitution ciphers and the principle underlying the Enigma Cipher Systems In all cipher systems one assumes that the message has been intercepted The objective is then to make it impossible, or PyEnigma is a Python 3 library for simulating the Enigma machines used by the German armed forces (Wehrmacht) during World War 2 PyEnigma makes it possible to both encrypt and decrypt messages that can be sent to, or received from, actual Enigma machines used by the German army (Heer), air force (Luftwaffe), and navy (Kriegsmarine) It is my hope that library will be useful to Enigma




The Enigma Machine Explained Youtube



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
The main focus of Turing's work at Bletchley was in cracking the 'Enigma' code The Enigma was a type of enciphering machine used by the German armed forces to send messages securely Although Polish mathematicians had worked out how to read Enigma messages and had shared this information with the British, the Germans increased its security at the outbreak of war by changing the cipherThe fact that the Enigma cipher was cracked was kept in the utmost secrecy even within the Polish General Staff's II Directorate The officers got the messages signed with a codename "Wicher" (that was the Enigma code break) that were considered fully reliable, but the source was classified In 1934, the General Staff's Cipher Office established a new site for their German branch (BS4)Enigma machines were widely used by Nazi Germany during the World War 2 British scientist Alan Turing, leveraging on earlier breakthrough by three Polish military intelligence cryptanalysts Marian Rejewski, Jerzy Różycki and Henryk Zygalski, led the effort to break the cipher Poor configuration and usage of the machine also facilitated the



Github Voandy Enigma Machine A Simulated Enigma Machine




Ukw D
Automatically crack and create well known codes and ciphers, and perform frequency analysis on encrypted texts CipherTools Crossword tools Other stuff Sudoku solver Maze generator JavaScript editor Ciphers Introduction Crack cipher texts Create cipher texts Enigma machine Find out about the substitution cipher and get messages automatically cracked and createdAlso, would anyone happen to know how I could do decryption properly?As technology increases, so do the methods of encryption and decryption we have at our disposal World War II saw wide use of various codes from substitution




How To Crack The Enigma Cipher Youtube




How To Build An Enigma Machine Virtualisation In Python By Vasile Păpăluță Analytics Vidhya Medium
This version of cryptii is no longer under active development Find the latest version on cryptiicom Cryptii is an OpenSource web application under the MIT license where you can encode and decode between different formatDuring World War II, the Germans used ENIGMA, a cipher machine, to develop nearly unbreakable codes for sending messages ENIGMA's settings offered approx 158,000,000,000,000,000,000 possible solutions, yet the Allies were eventually able to crack its code The machine was developed by the Dutch to communicate banking secrets The Germans bought the patent in 1923 for Background and Example This code simulates the Enigma machine, minus the plugboard Here's some test code that illustrates how the machine's construction and use >>> r1 = Rotor(" Stack Exchange Network Stack Exchange network consists of 178 Q&A communities including Stack Overflow, the largest, most trusted online community for developers to learn,




The Inner Workings Of An Enigma Machine Youtube




Enigma Richard Gallon We Are Here
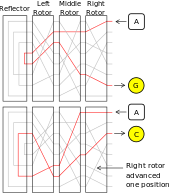
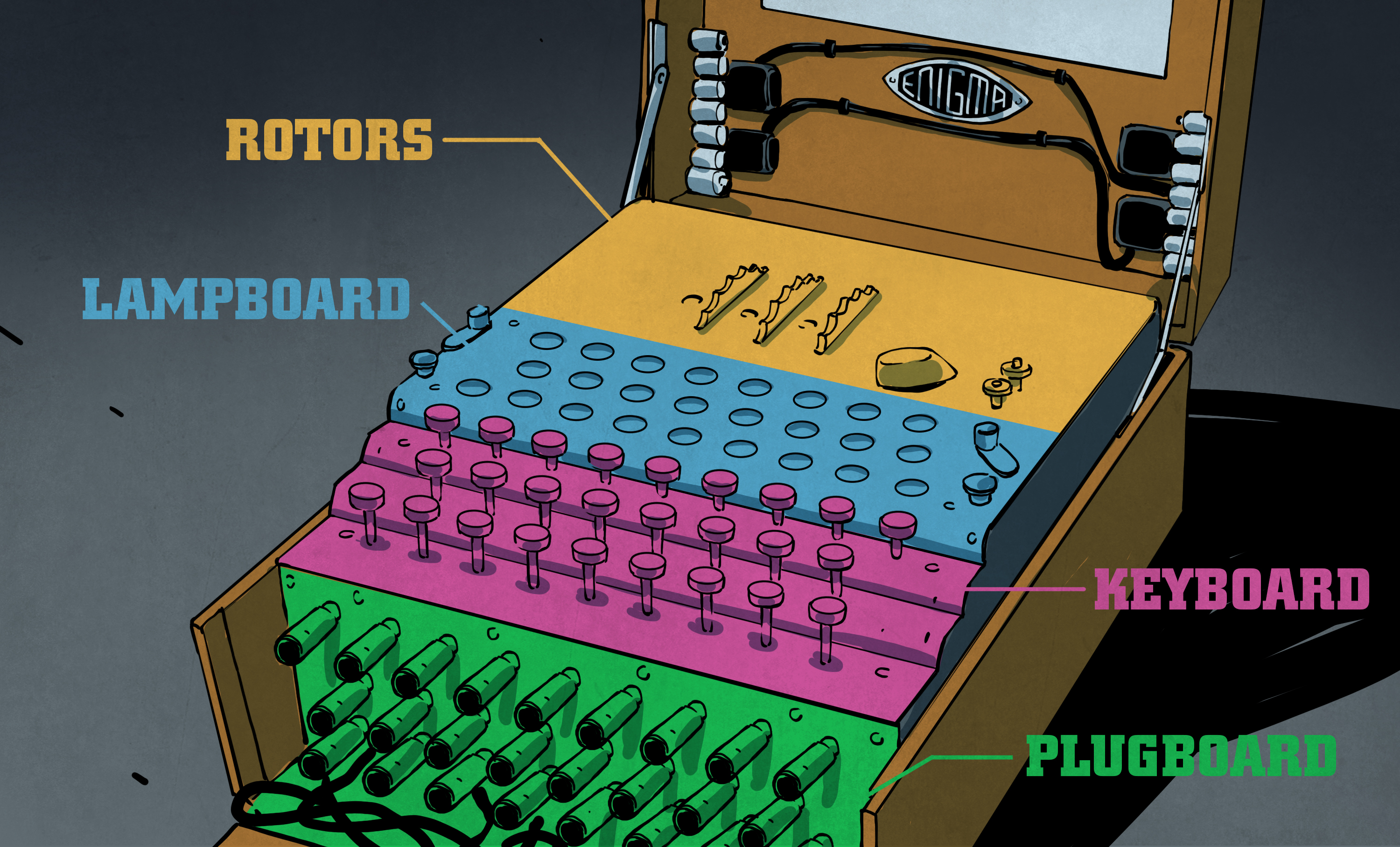
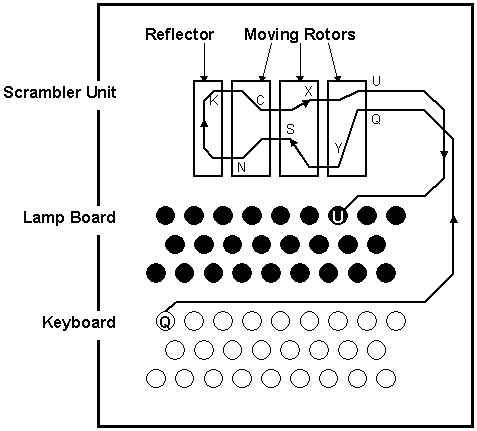
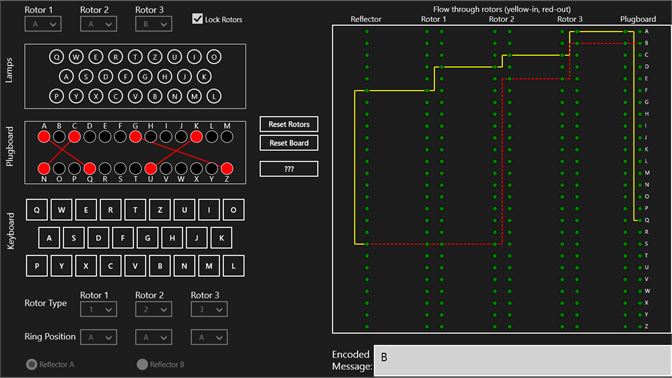
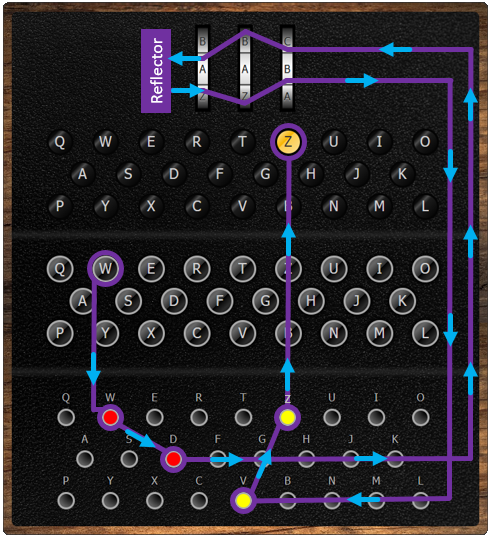
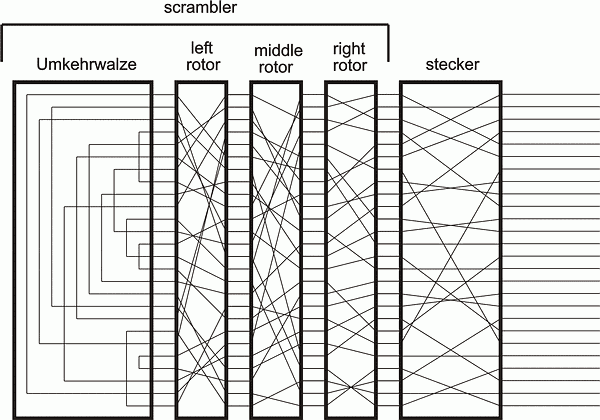
Each EnigmaI machine came with a set of 5 interchangeable electromechanical cipher wheels, known as rotors The rotors had 26 contacts on one side, and 26 pins on the other Three rotors would be placed into the machine on a shaft, with the pins of one connecting to the contacts of the next The rotors would then be set to prearranged positions, and the user wouldIntroduction, Binary Numbers, Error Detection, Secret Codes, The Enigma, Public Key CryptographyENIGMA was a cipher machine—each keystroke replaced a character in the message with another character determined by the machine's rotor settings and wiring arrangements that were previously established between the sender and the receiver For additional security, the German military services usually doubleencrypted their messages by first substituting original text with code



Enigma Machine Wikipedia



The Enigma Enigma How The Enigma Machine Worked Hackaday
The enigma machine was used in World War II to encrypt secret messagesThe Enigma machines are a series of electromechanical rotor cipher machines The first machines were invented at the end of World War I by German engineer Arthur Scherbius and were mainly used to protect commercial, diplomatic and military communication Enigma machines becameVigenère Cipher The Vigenère cipher was invented in the mid16th century and has ever since been popular in the cryptography and code In addition, the article seems to imply that the cryptanalysis of the ENIGMA was comparable to that of the substitution ciphers, which, if intended, is extremely misleading Also, the substitutions of the Enigma, in a given setting, would repeat only after 17,576 characters (or 456,976 in case of a four rotor ENIGMA), whereas the message lengths were, as per regulations,




Wolfenstein 2 How To Use The Enigma Codes And The Enigma Machine Youtube




Mechanical Setup Of The Enigma Machine From The Figure We Observe That Download Scientific Diagram
In this section, we will develop a bruteforce crypt attack on the Enigma cipher text using a Raspberry Pi A bruteforce attack is simply an exhaustive search over all possible machine settings to try and find which one was used For the time being, we will assume we know the plugboard settings Here is the intercepted message we need to decipher In addition to our cipher text, weThe Enigma machines produced a polyalphabetic substitution cipherDuring World War I, inventors in several countries realized that a purely random key sequence, containing no repetitive pattern, would, in principle, make a polyalphabetic substitution cipher unbreakable This led to the development of rotor cipher machines which alter each character in the plaintext to produce the The Enigma code, a very sophisticated cipher, was used during the Second World War by the Germans It involved an Enigma machine, similar to a typewriter, where pressing a letter would make the cipher letter light up on a screen The Enigma machine involved several wheels which connected letters with wires, determining which cipher letter would light up All Enigma



Enigma Simulator



Enigma And A Way To Its Decryption
Enigma cipher machine emulator (CLI library) written in Go emulator cli enigma enigmasimulator enigmamachine enigmacipher Updated ; Wie der Code der legendären EnigmaMaschine geknackt wurde Vor 80 Jahren kam es auf einem unscheinbaren Landsitz in Südengland zu einem historischen Durchbruch Zum ersten Mal gelang es britischen Codeknackern, die Verschlüsselung der legendären "Enigma" zu knacken – der Maschine, mit der die Deutschen im Zweiten Weltkrieg ihreThe Enigma machine Encrypt and decrypt online The Enigma cipher machine is well known for the vital role it played during WWII Alan Turing and his attempts to crack the Enigma machine code changed history Nevertheless, many messages could not be decrypted until today Punycode converter Base64 to text




Enigma Machine Wikipedia



Enigma Machine Beziehen Microsoft Store De De
The codebreaker then breaks the cipher text in a similar way to a Caesar cipher Auguste Kerckhoffs improved on Kasiski's method by matching each "column's letter frequencies to shifted plaintext frequencies to discover the key letter (Caesar shift) for that column" Once the codebreaker knows each letter in the secret key, all they have to do is decrypt the cipher text using a Enigma Decipher Victory, reveals the extent to which the input of Polish cryptographers made possible the breaking of Nazi Germany's Enigma code during World War Two Organised by Poland's Wielkopolska region and financed by the Polish Ministry of Foreign Affairs, a major exhibition, EnigmaDecipher Victory, has previously been on display in museumsCryptiiText to Enigma Cryptiiv2 Cryptii Convert, encode, encrypt, decode and decrypt your content online Attention!



Teaching History With 100 Objects Enigma Cipher Machine




Enigma Machine Wikimedia Commons
The enigma machine was used in World War II to encrypt secret messages The Enigma machines are a series of electromechanical rotor cipher machines The first machines were invented at the end of World War I by German engineer Arthur Scherbius and were mainly used to protect commercial, diplomatic and military communication Enigma machines becameAn elementary introduction to the way the famous Enigma code used by the Germans during WWII David Perry explains some of the history and the mathematics beCover German soldiers using an ENIGMA cipher machine in the field David Mowry served as a historian, researching and writing histories in the Cryptologic History Series He began his Agency career as a linguist in 1957 and later () held positions as a linguist and cryptanalyst From 1969 through 1981 he served in various technical and managerial positions In the latter part of




Enigma Machine Wikipedia



3
I asked on Stack Overflow and it wasn't received too well and one of the comments said codeThe Atbash Cipher is a really simple substitution cipher that is sometimes called mirror code It is believed to be the first cipher ever used To use Atbash, you simply reverse the alphabet, so A becomes Z, B becomes Y and so on Atbash Cipher Tool; At the core of an original Enigma machine lies a set of three or four rotors Each rotor hardwires pairs of letters together in its own unique pattern This acts as a basic substitution cipher



Enigma Encoder 101 Computing



Enigma Procedure
The enigma rotors The rotors are special gears with 26 pins Every pin is related to an English letter When an electric signal (in mechanical machine) comes to a An Enigma machine is a famous encryption machine used by the Germans during WWII to transmit coded messages An Enigma machine allows for billions and billions of ways to encode a message, making it incredibly difficult for other nations to crack German codes during the war — for a time the code seemed unbreakable Alan Turing and other researchers exploited a fewModern Codes, Atbash Cipher, Caesar Shift, Caesar Square, Anagrams, Substitution Ciphers, Other Ciphers Creating and decoding secret messages has played a pivotal role throughout history and in many fictional novels, from the Caesar Cipher by Julias Caesar, through to the Enigma Machine in World War II to the various codes in Dan Brown's novel The Da Vinci Code




Enigma Machine Wall Street International Magazine




Valuable German Wwii Enigma Machine Found In Flea Market News Dw 12 07 17




Zygalski Sheets Wikipedia




Enigma Machine Simulator Nazi Code Machine Youtube




Octapi Brute Force Enigma What Is Enigma And How Does It Work Raspberry Pi Projects




Hacking Homeschooling Codebreakers And Ww2 Histories Of The Unexpected




Home Make Diy Projects And Ideas For Makers Enigma Machine Ciphers And Codes Escape Room Puzzles




Ic211 Oop And Enigma



Enigma Machine



Enigma Codeproject




Enigma Rotor Details Wikipedia




Enigma I A Fully Operational Three Rotor Enigma I Cipher Machine Berlin Heimsoeth Und Rinke 1943 History Of Science And Technology Including Fossils Minerals And Meteorites Books Manuscripts Sotheby S



Enigma Encoder 101 Computing



3




Review Bletchley Park Block B Beaking The Enigma Code And The Bombe Machine
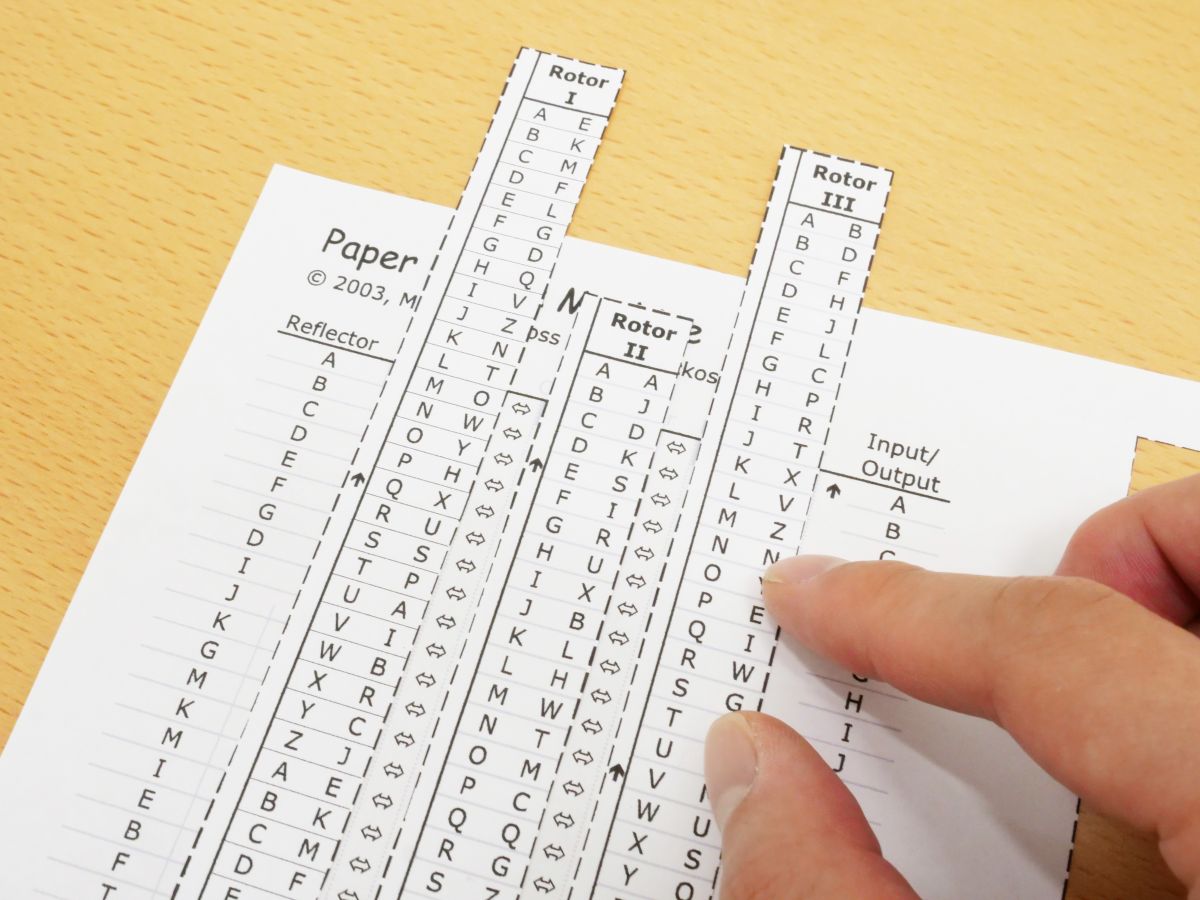



I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine




The Enigma Cipher Machine And Breaking The Enigma Code



Enigma The German Cipher Machine



What Alan Turing Can Teach Us About Product Management Chargebee S Saas Dispatch



The Encryption War Of Wwii The Enigma Encryption Machine Engineering And Technology History Wiki



Pdf The Cryptanalysis Of The Enigma Cipher The Plugboard And The Cryptologic Bomb




Enigma Machine Emulator 101 Computing




327 Code Enigma Photos Free Royalty Free Stock Photos From Dreamstime




Enigma Machine Wikipedia




Enigma Daily Settings Generator 101 Computing
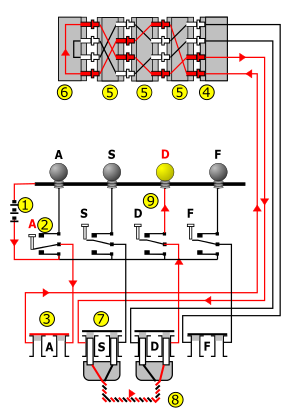



Enigma Machine Wikipedia



Enigma Procedure



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher




Pin On Science




Digitalocean Blog




Enigma Machine Wikipedia



The Polish Attack On Enimga




Enigma Machine Brilliant Math Science Wiki




How To Papercraft Enigma Machine Make




The Enigma 1
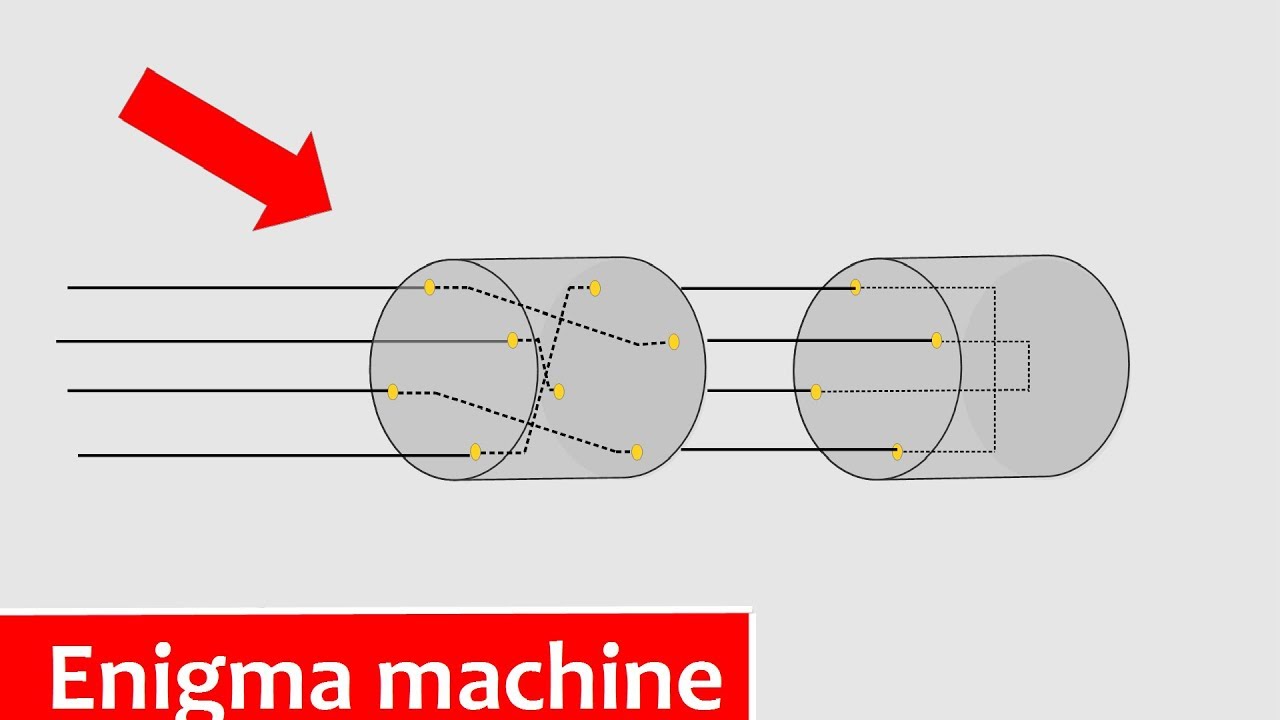



How The Enigma Machine Works Animation Youtube




How Did The Enigma Machine Work Computing The Guardian
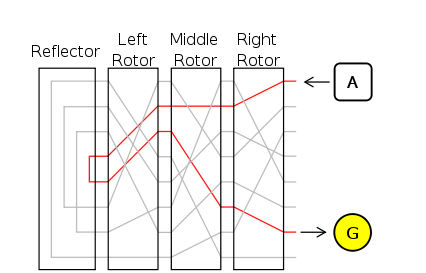



How To Build An Enigma Machine Virtualisation In Python By Vasile Păpăluță Analytics Vidhya Medium




Cryptanalysis Of The Enigma Wikipedia




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium




Rare German Enigma Code Machine Sells At Auction For 232 000




Operation Turing
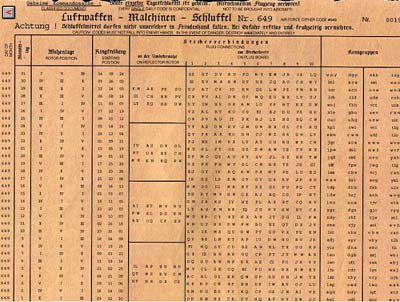



Exploring The Enigma Plus Maths Org




Cipher Machines From Antiquity To The Enigma Machine




Extremely Rare Wwii German Naval Airforce Secret Enigma Cipher Machine Code Book Cover




Enigma Cipher Ciphers Free Photo On Pixabay




M4




Dpma Enigma




Enigma Machine Simulator Program About Code Name Verity Spies Etc Enigma Aspectos Historia



Enigma Cipher




Enigma Cipher Machine



Fhcam Enigma Machine



Naval Enigma




Wolfenstein 2 Enigma Machine How To Decode Cards Gamerevolution




Wwii German Enigma Code Machine Manual 967



Gc1vz Darwin Enigma Challenge Unknown Cache In Northern Territory Australia Created By Gibbo003
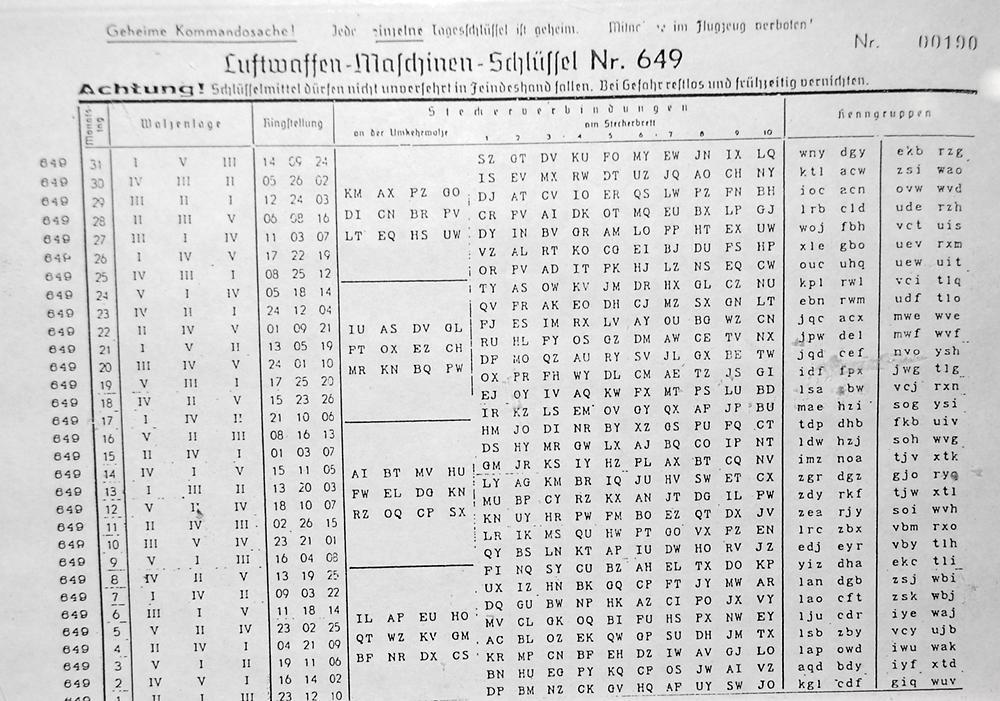



The Enigma Enigma How The Enigma Machine Worked Hackaday




Enigma Entschlusselung Wie Schachspieler Halfen Den Krieg Zu Gewinnen Der Spiegel



The Polish Attack On Enimga




Nazi Enigma Code Machine Like In Imitation Game Goes To Auction Bloomberg
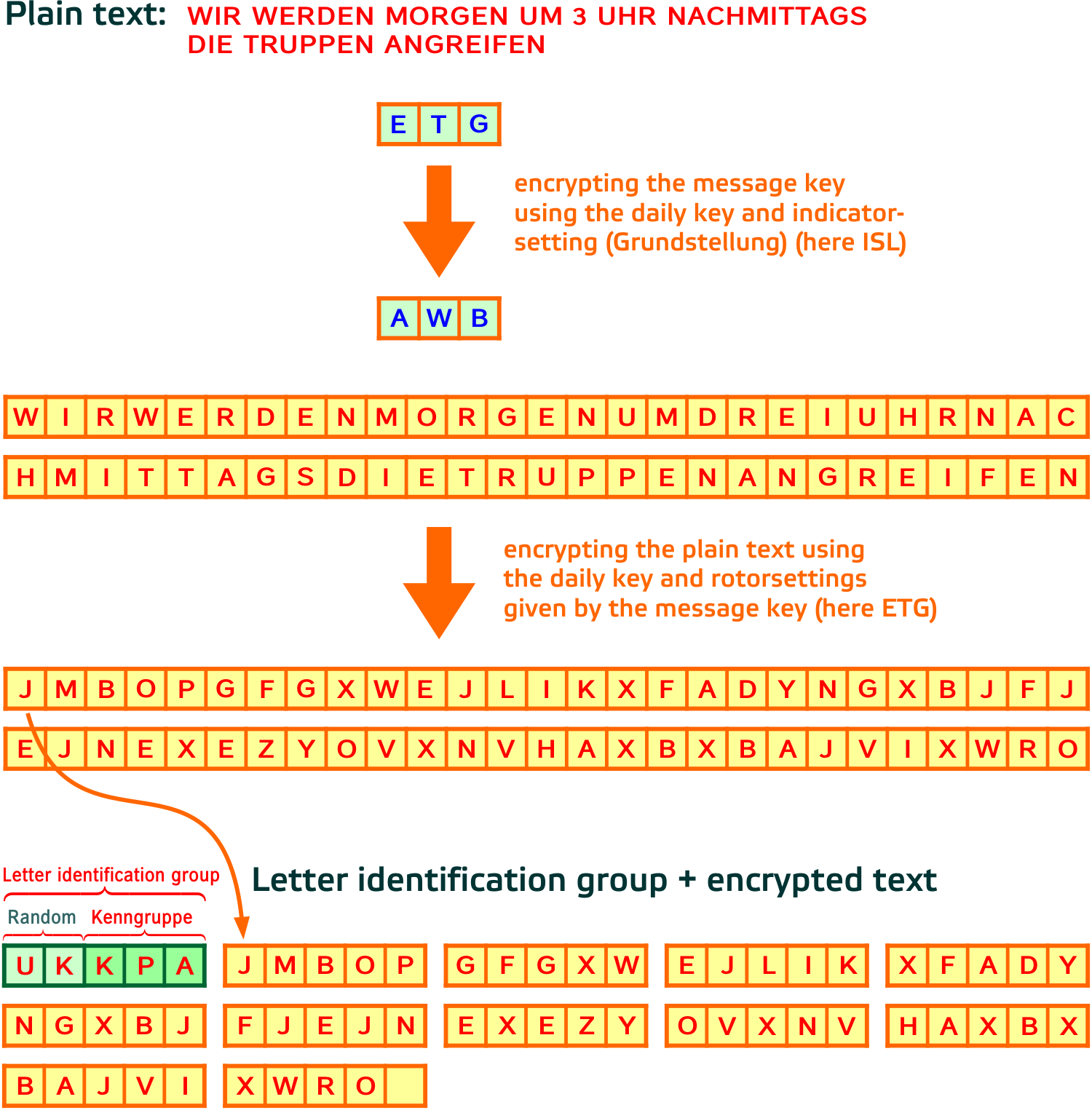



Enigma The German Cipher Machine
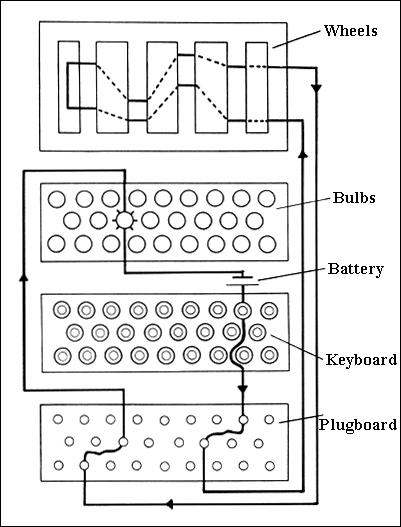



Enigma Machine
/https://tf-cmsv2-smithsonianmag-media.s3.amazonaws.com/filer/86/67/86675eae-746c-4761-b4ed-441014c487b5/stellnetz-bergung-enigma_fund-c-florian_huber-submaris.jpg)



Divers Discover Nazi Enigma Machine Thrown Into The Baltic Sea During Wwii Smart News Smithsonian Magazine




A Student Has Rebuilt The Machine That First Cracked German Enigma Codes Zdnet
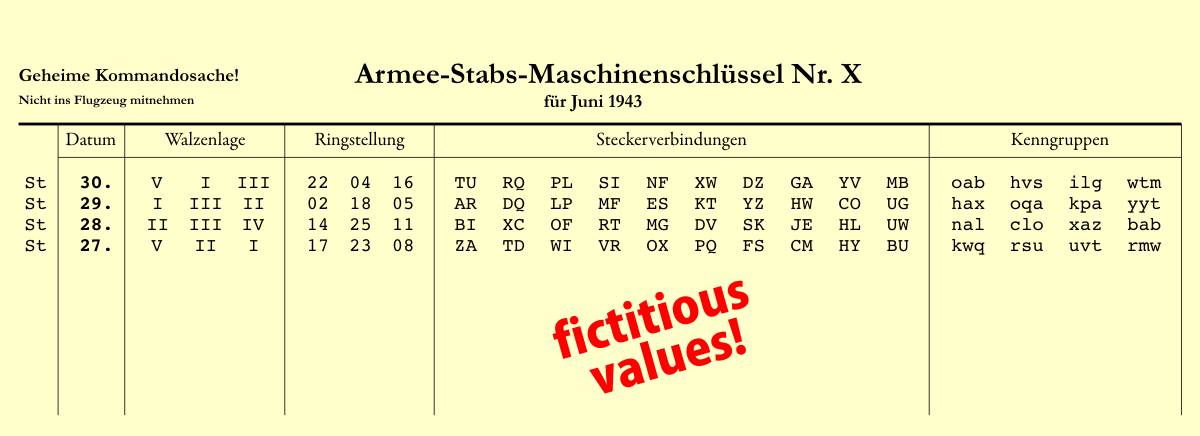



Enigma The German Cipher Machine




Enigma Machine Wikipedia




Phalanx The Enigma Machine It May Be Roundly Asserted That Human Ingenuity Cannot Concoct A Cipher Which Human Ingenuity Cannot Resolve Edgar Allan Poe 1841 Cryptography Is As Ancient As



2




Keyboard Of A Nazi German Enigma Cipher Machine Used During World War Ii To Develop Nearly Unbreakable Codes For Sending Messages The Enigma S Settings Offered 150 000 000 000 000 000 000 Possible Solutions Allied Efforts Based In




Extremely Rare Wwii German Aviator School Secret Enigma Cipher Machine Code Book Cover



1




Breaking The Code The Secrets Of Enigma Cipher Machines Books Manuscripts Sotheby S



1




The History And Technology Of The Enigma Cipher




Enigma Definition Machine History Alan Turing Facts Britannica




Operation Turing




Breaking Enigma A Story Of European Co Operation Science Museum Blog



Enigma C




Paper Enigma Machine Youtube
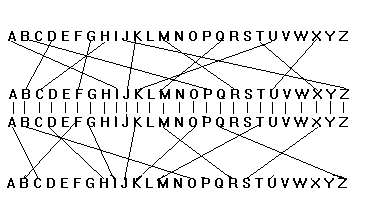



The Enigma 1



2




Bombe Wikipedia



0 件のコメント:
コメントを投稿